If You Know a Decryption Key Can You Find the Encryption Key
At PreVeil we often discover ourselves explaining to our customers the concepts of how public and private keys work. We thought it would be helpful to talk over what these keys are, what they aren't, and how they piece of work.
The blog below provides a general overview on public and individual key pairs rather than an architectural overview of PreVeil. For a detailed understanding of PreVeil's public-private central architecture, please check out our architectural whitepaper.
How public and private fundamental encryption works
Public and private keys form the basis for public central cryptography , also known as disproportionate cryptography. In public key cryptography, every public key matches to only one private key. Together, they are used to encrypt and decrypt messages. If you encode a message using a person's public key, they can simply decode it using their matching individual key.
Public and private keys: an example
Bob wants to ship Alice an encrypted email. To do this, Bob takes Alice'southward public key and encrypts his message to her. Then, when Alice receives the message, she takes the private key that is known but to her in order to decrypt the message from Bob.
Although attackers might attempt to compromise the server and read the message, they volition be unable to because they lack the private cardinal to decrypt the message. Only Alice volition be able to decrypt the bulletin as she is the only one with the private central. And, when Alice wants to respond, she simply repeats the process, encrypting her message to Bob using Bob's public fundamental.
![]()
More than on how public and private keys are used:
Whitepaper: PreVeil Security and Design
Commodity: End-to-terminate encryption
![]()
The difference between public and private keys
Public keys have been described by some as being like a concern' address on the web – it's public and anyone tin can look information technology up and share it widely. In disproportionate encryption, public keys can be shared with everyone in the organization. Once the sender has the public key, he uses it to encrypt his bulletin.
Each public key comes paired with a unique private key. Call up of a individual fundamental as alike to the key to the front door of a business organisation where simply you have a copy. This defines i of the main differences betwixt the 2 types of keys. The private key ensures only y'all tin get through the front door. In the case of encrypted messages, y'all employ this private key to decrypt messages
Together, these keys aid to ensure the security of the exchanged data. A bulletin encrypted with the public primal cannot be decrypted without using the respective private key.

Generating public and private keys
The public and individual key are non actually keys but rather are actually large prime number numbers that are mathematically related to one another. Being related in this case means that whatever is encrypted past the public key tin only exist decrypted by the related private key.
A person cannot guess the private key based on knowing the public key. Considering of this, a public key tin can be freely shared. The individual key however belongs to merely ane person.
There are several well-known mathematical algorithms that are used to produce the public and private key. Some well-respected algorithms include:
- Rivest-Shamir-Adelman (RSA) – Oldest of the public-individual central cryptography systems. Frequently used to transmit shared keys for symmetric primal cryptography
- Digital Signature Standard (DSS) – a Federal Information Processing Standard specifying the algorithms that tin can be used to generate digital signatures used by NIST
- Elliptic curve cryptography (ECC)– As its name implies, ECC relies on elliptic curves to generate keys. Often used for key agreement and digital signatures. At PreVeil, we utilise elliptic-curve cryptography's Curve-25519 and NIST P-256.
Summary Public key cryptography
Public key cryptography provides the basis for securely sending and receiving messages with anyone whose public key you can access.
Public keys enable:
- Users to encrypt a message to other individuals on the organization
- You lot can confirm a signature signed by someone'southward private cardinal
Private keys enable:
- Yous tin can decrypt a message secured by your public primal
- You can sign your bulletin with your private key and so that the recipients know the message could merely take come from you.
Public-private key encryption: Real world examples
Digital signatures
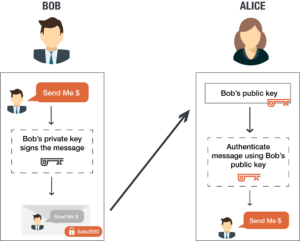
Public and private keys can also exist used to create a digital signature. A digital signature assures that the person sending the message is who they claim to be.
Typically, we use the recipient's public key to encrypt the data and the recipient then uses their private key to decrypt the data. However, using the scheme of digital signatures, there'southward no style to authenticate the source of the message. Mike could go a hold of Alice's public key (since it'southward public) and pretend that Bob is the person sending a message to Alice.
To create a digital signature, Bob digitally signs his electronic mail to Alice using his private primal. When Alice receives the bulletin from Bob, she tin can verify the digital signature on the message came from Bob by using his public fundamental. As the digital signature uses Bob's individual key, Bob is the merely person who could create the signature.
PreVeil'south method for securing letters is a scrap more complex than the example provided in a higher place. However, the example provides a good full general overview for how asymmetric encryption works.
Diffie-Helman key exchange
The Diffie Hellman key exchange demonstrates an example of how users tin securely exchange cryptographic keys over a public channel.
In the past, secure encrypted communication required that the individuals first substitution keys by a secure means such equally paper primal lists transported by a trusted courier. The Diffie–Hellman key exchange method allows two parties that have no prior cognition of each other to jointly establish a shared clandestine cardinal over an insecure channel.
PreVeil uses the Diffie Hellman cardinal exchange to enable Web PreVeil. Spider web PreVeil is a browser based end-to-terminate encrypted email service that allows users to hands access their secure email account on the spider web without any software download or whatever passwords to remember.
Here'southward a video to explicate how this works:
![]()
Business benefits of public private primal encryption
By using a public and individual key for encryption and decryption, recipients can be confident that the data is what the sender says it is. The recipient is assured of the confidentiality, integrity and authenticity of the data.
Confidentiality is ensured because the content that is secured with the public central can only be decrypted with the private key. This ensures that only the intended recipient can always review the contents
Integrity is ensured because part of the decryption process requires checking that the received message matches the sent message. This ensures that the message has not been changed in betwixt.
Authenticity is ensured because each message sent by Alice to Bob is also signed by Alice's private fundamental. The only mode to decrypt Alice's private central is with her public fundamental, which Bob can access. By signing the message with her individual key, Alice ensures the authenticity of the message and shows that information technology really did come from her.
![]()
Conclusion
Public and individual cardinal pairs course the ground for very strong encryption and data security. If y'all are interested in reading more about public and private keys, take a look at the following articles:
- Finish-to-terminate encryption
- Passwordless authentication
- PreVeil technology
Source: https://www.preveil.com/blog/public-and-private-key/
Post a Comment for "If You Know a Decryption Key Can You Find the Encryption Key"